Hidden Crypto-Mining Malware: How To Detect And What To Do

Table of Contents
The cryptocurrency rush has become a real problem for computer users. First, mining has devastated the market of video cards, game consoles, and even some components for assembling cars. Secondly, computers are now suffering from a new type of attack — cryptocurrency is mined not only on special farms but also on the systems of ordinary users. Cryptocurrency Malware is responsible for this epidemic, which impacts the performance of the computer. But it is easy to detect and eliminate them if you know a few tricks.
What is a virus?
A computer virus is so-called because it acts like a natural virus — for example, such as the flu. Infected particles get into the computer in various ways — these can be files that disguise themselves as important libraries, crawl into the boot sector of the system, and control the computer’s operation at a low level.

Viruses also include malicious programs that try to look like “useful” projects, are embedded in the software code, and start working only after the user installs the media program and grants it full rights to manage the computer. Such viruses are called Trojan horses — in honor of the eponymous “gift” of the Achaeans who are at war with Troy.
Crypto-Mining Malware
The Trojan type of computer viruses also includes Crypto-Mining Malware. Unlike classic Trojans, the new malware is designed to spread among the systems of private users — they do not need information, passwords, and credit card data. These viruses are only interested in the hardware capabilities of the computer — they mine cryptocurrency. Such “viruses” can be divided into two groups:
Typical Crypto-Mining Malware
This is a ready-made archive with a program that can be distributed either separately or bundled with any other program. As a rule, this malware is installed in the background and automatically runs during the computer boot. Of course, they are called viruses only out of habit this is a regular miner program that is used by owners of mining farms to extract coins. Hackers only slightly modify the program so that it can be deployed and activated in the system independently.

The only difference between Crypto-Mining Malware and the miner where the profit goes is that the usual program mines coins to the wallet of the farm owner, and the malware transfers the mined coins to the hacker’s wallet.
Cryptojacking
The second type of this malware is cryptojacking. Instead of being installed in the system, the Crypto-Mining Malware exists as a script embedded in the site. As soon as the visitor gets to the web page, the script is activated, and the miner begins to mine cryptocurrency. In some cases, this method replaces the site owner’s earnings on advertising. At the same time, a conscientious resource speaks openly about this and warns visitors that instead of displaying advertising banners and ads. It will use the hardware capabilities of the system to its advantage. Such activity cannot be called viral — everything happens openly, officially, and only with the permission of the computer owner.

Another thing is if the website hides mining activity and uses the power of the processor or video card without warning. As a rule, such resources use the hardware capabilities of the computer in bad faith — instead of 10-20% of the computer time, they take up all 100%. It is easy to get to such a website on the Internet — these are websites with a huge amount of advertising.
What is the danger of cryptocurrency mining malware?
Although Crypto-Mining Malware does not steal information and passwords, the harm from them can be much more extensive than from ordinary viruses. For effective cryptocurrency mining, the computer needs to use as much power as possible, so the infected computer extracts currency on the processor and video card, as well as using a disk drive. And even a short operation of the system in this mode can lead to overheating of the computer or failure of components.

If the problem with an increase in temperature seems insignificant to the owner of a desktop computer, then a laptop user can easily get a “brick” after a couple of hours of such roasting. But even if the hardware of the mobile system can withstand the test of mining, the device’s battery may run out at the most inopportune moment.
How to find and eliminate the virus
There are two ways to determine that third—party software uses a computer for selfish purposes-by certain actions of the device or using special programs.
The symptoms of infection with a Crypto-Mining Malware are easy to recognize by the behavior of the system — if ordinary viruses can quietly exist in the system, then the Crypto-Mining Malware immediately gives itself out after it gets to the disk and is activated.
Signs:
- strong heating of the computer
- increased cooling noise
- slow operation of the system due to a full load of all processor cores and video cards
You can experience all the same signs if you run a demanding game or a task for rendering a 3D scene in high resolution on your computer, and then try to stream a video on YouTube.
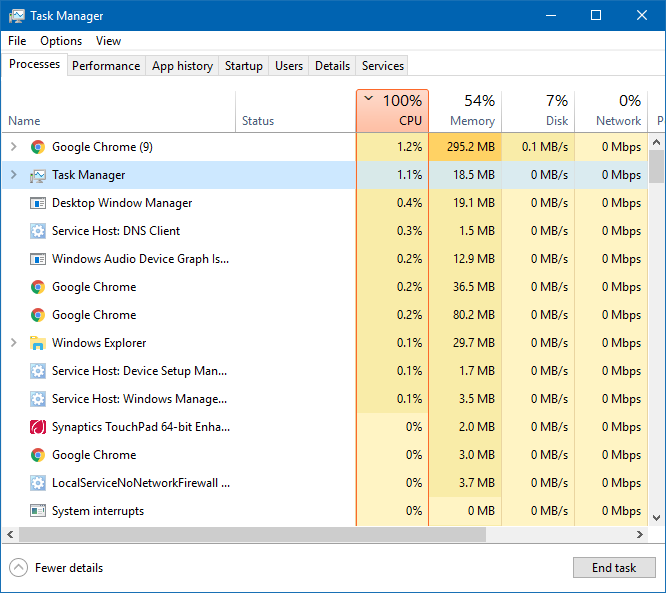
Previously, users could easily detect Crypto-Mining Malware by an unfamiliar process in the task manager, as well as by excessive loading of cores or video card memory.
The current versions of the malware have become much smarter, so even an experienced master will not be able to determine which program loads the system and where to find it. For example, the standard “look in the task manager” method no longer works — viruses know their weaknesses and carefully hide them. By the time the user wants to press the Ctrl-Alt-Del key combination, Crypto-Mining Malware will safely disconnect and will wait for the next best case for activation.
The only place where a virus miner can give itself away during operation is the temperature of the components. Temperature sensors and heated surfaces have high inertia, so within a few minutes after the virus is turned off, the computer will show a temperature higher than that which should be during the quiet operation of the system.
Viruses are skillfully hidden from third-party programs and system monitors, so it also does not make sense to use them to search for Crypto-Mining Malware. It is better to leave this matter to specialized software — for example, an antivirus.
Defenders of computer health
Any popular antivirus is suitable for finding and removing threats on your home computer. For example, ESET NOD32 Internet Security is a comprehensive solution for system protection. This set includes not only antivirus, but also a firewall that closes access to the system from the outside, and also prohibits unknown processes from accessing the Internet without the user’s permission. This means that the Crypto-Mining Malware will not be able to mine just because he was forbidden to communicate with the network. The same can be said about other antiviruses.

The problem is that the antivirus built into Windows has only a part of the skills that paid software has. There are quite a lot of such vulnerable systems in the world — users are chasing every percent of the building power and neglect security in favor of the stability of the gameplay. In turn, viruses know how to bypass Windows obstacles, so the probability of catching malware tends to the maximum — and there is also an optimal solution for such users. The use of special antiviruses.
Browser Protection
Despite the extensive capabilities of antiviruses, Crypto-Mining Malware embedded in the site is not blocked by these programs and this causes even more inconvenience to the user.
Special browser extensions can be used to flexibly manage the operation of scripts on websites. For example, an extension for blocking ads of the AdBlock and type-it can block not only ad blocks and ads but also can configure custom filtering rules. For example, to prohibit the operation of a certain script on all sites.
Links to mining scripts in HTML format have long been known, so it is not difficult to block the execution of such malware. To do this, you need to specify the path to the script to the blocker and save the new filter. Naturally, the” market ” of s is developing. Therefore, in order not to chase links to block other new and little-known malware, you will have to use something more universal.
For example, install an anti-mining malware extension.
Go to the Google Chrome extension store, and enter the search query ” mining/miner blocker “.
These extensions are constantly updated and know more about Crypto-Mining Malwares than you can imagine. If Crypto-Mining Malware gets to the disk, an antivirus will meet him there. And the user now knows that a noisy and hot computer is not only an excuse to blow the system out of the dust, but also to check the system for viruses.
